Notes:
IAM
The following facts apply to IAM Groups:
Groups are collections of users and have policies attached to them.
A group is not an identity and cannot be identified as a principal in an IAM policy.
Use groups to assign permissions to users.
IAM groups cannot be used to group EC2 instances.
Only users and services can assume a role to take on permissions (not groups).
IAM roles can be used to access cross-account resources.
User IAM roles and tasks to assign specific permissions on AWS ECS
LOAD BALANCER
To add high availability to this architecture both the web tier and database tier require changes. For the web tier an Auto Scaling group across multiple AZs with an ALB
ALB load balancer: receives a request, it evaluates the listener rules in priority order to determine which rule to apply and then selects a target from the target group for the rule action. You can configure listener rules to route requests to different target groups based on the content of the application traffic.
Network Load Balancer operates at the connection level (Layer 4), routing connections to targets - Amazon EC2 instances, microservices, and containers – within Amazon Virtual Private Cloud (Amazon VPC) based on IP protocol data.
Classic Load Balancer provides basic load balancing across multiple Amazon EC2 instances and operates at both the request level and connection level. Classic Load Balancer is intended for applications that were built within the EC2-Classic network.
Auto Scaling
An Auto Scaling group contains a collection of Amazon EC2 instances that are treated as a logical grouping for the purposes of automatic scaling and management.
ASG Lifecycle hooks enable you to perform custom actions by pausing instances as an Auto Scaling group launches or terminates them. For example, you could install or configure software on newly launched instances, or download log files from an instance before it terminates.
Auto Scaling group scheduled action - To configure your Auto Scaling group to scale based on a schedule, you create a scheduled action
Amazon EC2 Auto Scaling supports the following types of scaling policies:
Target tracking scaling - Increase or decrease the current capacity of the group based on a target value for a specific metric. This is similar to the way that your thermostat maintains the temperature of your home – you select a temperature and the thermostat does the rest.
Step scaling - Increase or decrease the current capacity of the group based on a set of scaling adjustments, known as step adjustments, that vary based on the size of the alarm breach.
Simple scaling - Increase or decrease the current capacity of the group based on a single scaling adjustment.
Default termination policy:
If there are instances in multiple Availability Zones, choose the Availability Zone with the most instances and at least one instance that is not protected from scale in. If there is more than one Availability Zone with this number of instances, choose the Availability Zone with the instances that use the oldest launch configuration.
Determine which unprotected instances in the selected Availability Zone use the oldest launch configuration. If there is one such instance,terminate it.
If there are multiple instances to terminate based on the above criteria, determine which unprotected instances are closest to the next billing hour. (This helps you maximize the use of your EC2 instances and manage your Amazon EC2 usage costs.) If there is one such instance, terminate it.
If there is more than one unprotected instance closest to the next billing hour, choose one of these instances at random.
- ASG Cooldown period: Its default value is 300 seconds and it ensures that the Auto Scaling group does not launch or terminate additional EC2 instances before the previous scaling activity takes effec
AWS Global Accelerator VS CloudFront:
- AWS Global Accelerator: this service is used for directing users to different instances of the application in different regions based on latency. (điều hướng user gửi request tới các instances khác nhau ở các regions khác nhau dựa trên latency (độ trễ)) => AWS Global Accelerator: Provides you with static anycast IP addresses that serve as a fixed entry point to your applications hosted in one or more AWS Regions
- Cloud front: supports geoblocking
Cloud Front geo restriction can allow users on whitelist countries can access content and deny users on blacklist countries to access content
CloudFront signed URLs and signed cookies provide the same basic functionality: they allow you to control who can access your content. If you want to serve private content through CloudFront and you're trying to decide whether to use signed URLs or signed cookies, consider the following:
Use signed URLs for the following cases:
You want to use an RTMP distribution. Signed cookies aren't supported for RTMP distributions.
You want to restrict access to individual files, for example, an installation download for your application.
Your users are using a client (for example, a custom HTTP client) that doesn't support cookies.
Use signed cookies for the following cases:
You want to provide access to multiple restricted files, for example, all of the files for a video in HLS format or all of the files in the subscribers' area of a website.
You don't want to change your current URLs.
If using an ELB, it is best to enable ELB health checks as otherwise EC2 status checks may show an instance as being healthy that the ELB has determined is unhealthy. In this case the instance will be removed from service by the ELB but will not be terminated by Auto Scaling
More information on ASG health checks:
By default uses EC2 status checks.
Can also use ELB health checks and custom health checks.
ELB health checks are in addition to the EC2 status checks.
If any health check returns an unhealthy status the instance will be terminated.
With ELB an instance is marked as unhealthy if ELB reports it as OutOfService
A healthy instance enters the InService state.
If an instance is marked as unhealthy it will be scheduled for replacement.
If connection draining is enabled, Auto Scaling waits for in-flight requests to complete or timeout before terminating instances.
The health check grace period allows a period of time for a new instance to warm up before performing a health check (300 seconds by default).
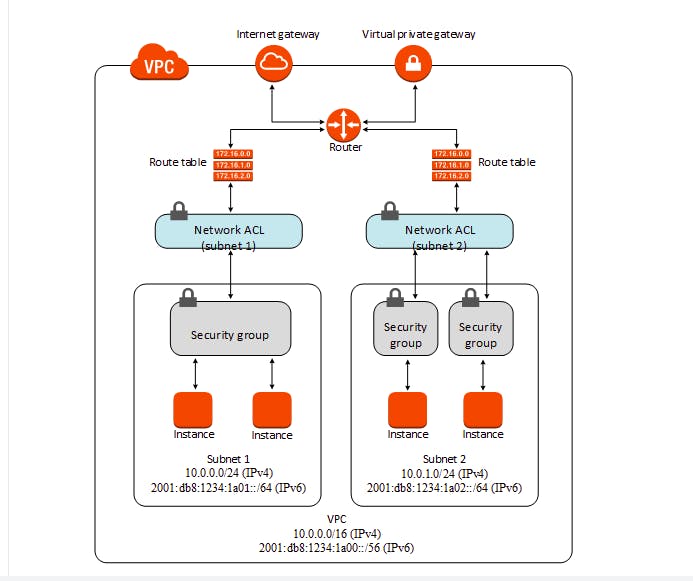
3. VPC
Steps to create simple VPC:
- Create VPC
- Create subnet Subnet
- Tạo internet gateway => attach to VPC: mỗi VPC chỉ có duy nhất 1 internet gateway
- Tạo route table => config route of route-table to target to Internet gateway then associate route-table với public subnet
1 route table có thể đính với nhiều subnet, nhưng 1 subnet chỉ đc attach với 1 route table
Attach an internet gateway to your VPC.
- Add a route to your subnet's route table that directs internet-bound traffic to the internet gateway.
- Ensure that instances in your subnet have a globally unique IP address
Ensure that your NACL and security group rules allow the relevant traffic to flow to and from your instance.
Security group: A security group acts as a virtual firewall for your instance to control inbound and outbound traffic. When you launch an instance in a VPC, you can assign up to five security groups to the instance. Security groups act at the instance level, not the subnet level. Therefore, each instance in a subnet in your VPC can be assigned to a different set of security groups.
Site-to-Site VPN: encrypted network connectivity between the on-premises data center and AWS Cloud
VPC Peering: tạo connect giữa 2 VPC
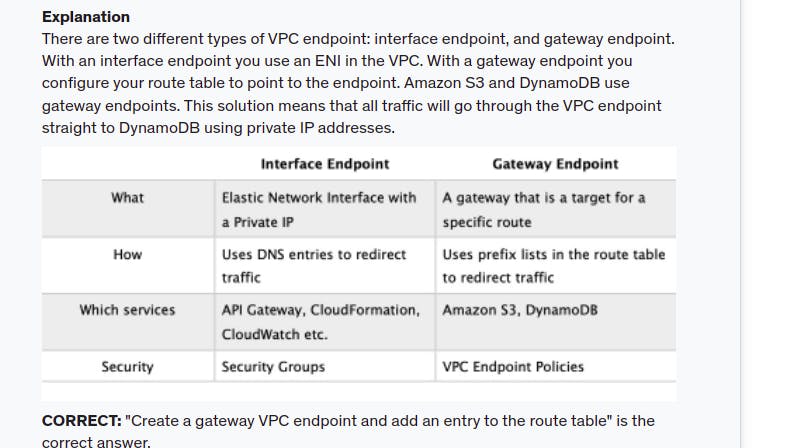
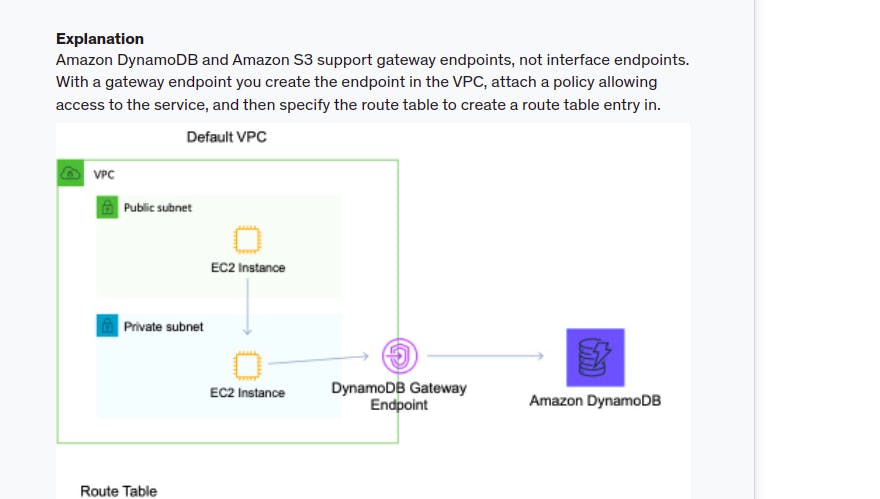
- VPC Endpoint: 2 loại VPC endpoint:
Gateway endpoint: tạo connect với aws services S3, DynamoDB từ private instance (attach to private subnet) in VPC mà ko cần internet-gateway
Interface endpoint : các service còn lại
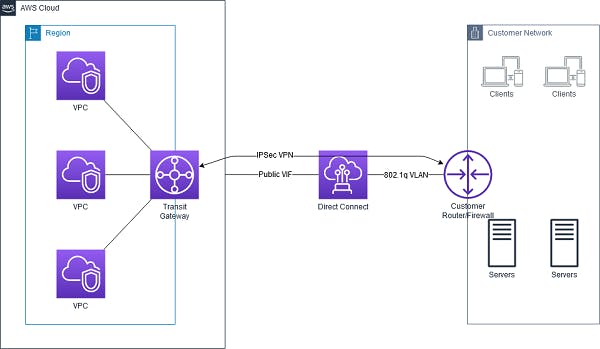
- AWS Transit Gateway Used to connect the Amazon VPCs to the on-premises networks through a central hub.
The Transit VPC can be used to enable connectivity between various VPC’s in different regions and customer data centers.
AWS Direct Connect: used to establish a dedicated network connection from your premises to AWS. Move GB/s of data to the cloud, over a p rivate secure network
VPN CloudHub: If you have multiple AWS Site-to-Site VPN connections, you can provide secure communication between sites using the AWS VPN CloudHub. This enables your remote sites to communicate with each other, and not just with the VPC.
Bashtion host: là 1 public instance cho phép connect bằng SSH tới instance ở trong private subnet
- EC2 instances in a private subnet can communicate with the Internet not just by having an Elastic IP, but also with a public IP address via a NAT Instance or a NAT Gateway.
Site to site VPN: connect your on-premises network or branch office site to your Amazon Virtual Private Cloud (Amazon VPC).
VPC console: 4 options: +. VPC with a single public subnet +. VPC with a private subnet only and AWS Site-to-Site VPN access +. VPC with public and private subnets and AWS Site-to-Site VPN access +. VPC with public and private subnets (NAT)
- VPC Flow Logs to capture detailed information about the traffic (source, destination, protocol) going to and from your Elastic Load Balancer. Need create a flow log for each network interface for load balancer.
- Subnets
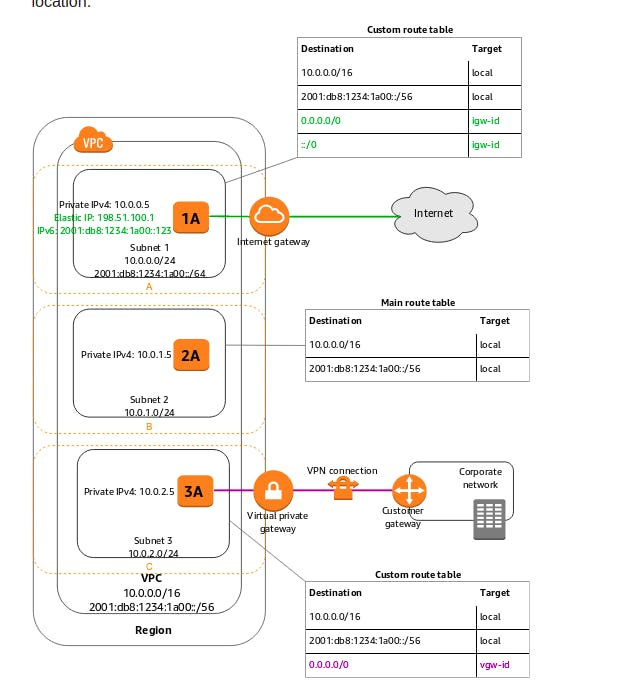
Below are the important points you have to remember about subnets:
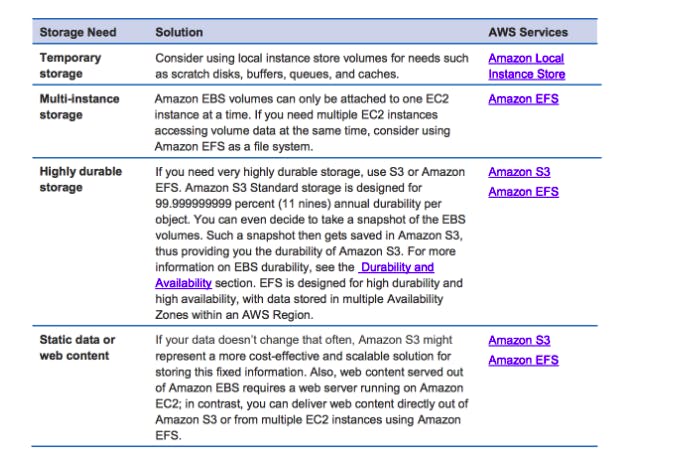
AWS STORAGES:
- Object storage => S3. Using Athena(serverless) to query, analysis data : Most cost-effective
- File storage:
+ EFS: FS is a network file system but for Linux only + Amazon FSx For Lustre: high perfomance + Amazon FSx for Windows File Server - Block storage => EBS
EBS STORAGE TYPE(iO1,sc1...),
EBS can provide lowest latency access for EC2 instance
EBS RAID0: for improve performance
- EBS RAID1: for improve fault tolerance
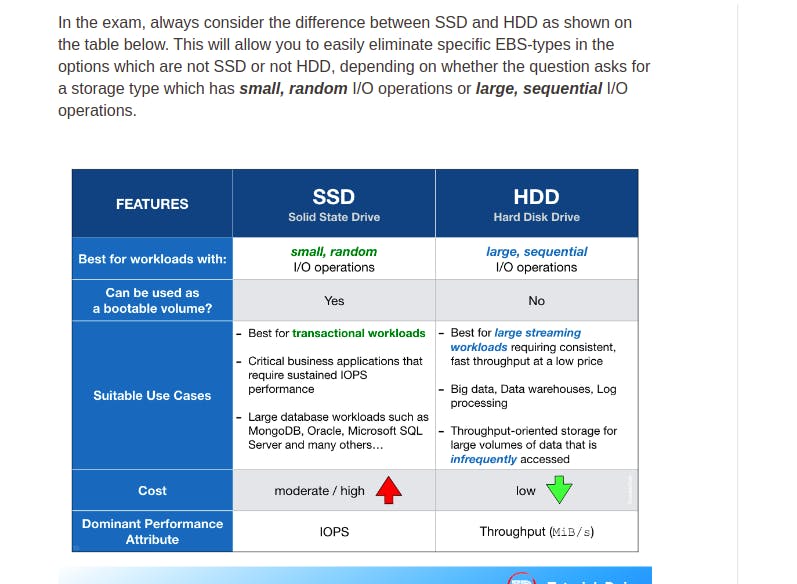
- SSD => high IOPS => best for transaction workloads
- HDD => high thoughputs => large streaming workloads
EBS volume types: 6 Types:
- [HDD] Cold: => max IOPS/Volume of 250, lowest cost storage, use for data data that is infrequently accessed
- [HDD] Throughput Optimized – (st1): => max IOPS/Volume of 500 great for database workload
- [SSD] General Purpose => max IOPS/Volume of 16,000.
- [SSD] Provisioned IOPS => 64,000 IOPS, I/O intensive database and high performance
- Encrypted Amazon EBS volume using AWS KMS.
- Amazon Data Lifecycle Manager (Amazon DLM) to automate the creation, retention, and deletion of snapshots taken to back up your Amazon EBS volumes
Here is a list of important information about EBS Volumes:
When you create an EBS volume in an Availability Zone, it is automatically replicated within that zone to prevent data loss due to a failure of any single hardware component.
An EBS volume can only be attached to one EC2 instance at a time.
By default, the root EBS volume is deleted (attribute enabled) and any other EBS attached is not deleted.
After you create a volume, you can attach it to any EC2 instance in the same Availability Zone
An EBS volume is off-instance storage that can persist independently from the life of an instance. You can specify not to terminate the EBS volume when you terminate the EC2 instance during instance creation.
EBS volumes support live configuration changes while in production which means that you can modify the volume type, volume size, and IOPS capacity without service interruptions.
Amazon EBS encryption uses 256-bit Advanced Encryption Standard algorithms (AES-256)
EBS Volumes offer 99.999% SLA.
– These volumes can burst up to 80 MB/s per TB, with a baseline throughput of 12 MB/s per TB and a maximum throughput of 250 MB/s per volume
HDD, Magnetic – Standard – cheap, infrequently accessed storage – lowest cost storage that can be a boot volume.
- EC2 instance store volumes: provide The best I/O performance, data sẽ mất khi instance bị terminate
EBS (network drive): data ko bị mất khi instance terminated - NOT for multi-AZ deployments.
EFS – Elastic File System (only Linux): (network file system) that can be mounted on many EC2
FSx for Windows: Highly durable and available file systems that can span multiple availability zones (AZs) for windows files server
AWS Storage Gateway: dùng để truy cập vào file đặt tại local premise server. Gồm 3 loaại :
- File access / NFS => File Gateway
- Volumes / Block Storage / iSCSI => Volume gateway
- VTL Tape solution / Backup with iSCSI = > Tape Gateway
NFS file => Can use either Amazon EFS or AWS Storage Gateway – File Gateway. Nhưng Storage Gateway hỗ trợ bởi S3 nên support Availability and Durability
Amazon FSx for Lustre makes it easy and cost-effective to launch and run the world’s most popular high-performance file system.
Amazon FSx for Windows File Server is a fully managed Microsoft Windows file system with full support for the SMB protocol, Windows NTFS, Microsoft Active Directory ( AD ) Integration.
Amazon EMR - Amazon EMR is the industry-leading cloud big data platform for processing vast amounts of data using open source tools such as Apache Spark, Apache Hive, Apache HBase, Apache Flink, Apache Hudi, and Presto.
AWS Glue - AWS Glue is a fully managed extract, transform, and load (ETL) service that makes it easy for customers to prepare and load their data for analytics.
- S3 (such as parallel processing, related to read after write consistency, Encryption)
- Enable versioning on the bucket - Versioning is a means of keeping multiple variants of an object in the same bucket. You can use versioning to preserve, retrieve, and restore every version of every object stored in your Amazon S3 bucket. Versioning-enabled buckets enable you to recover objects from accidental deletion or overwrite.
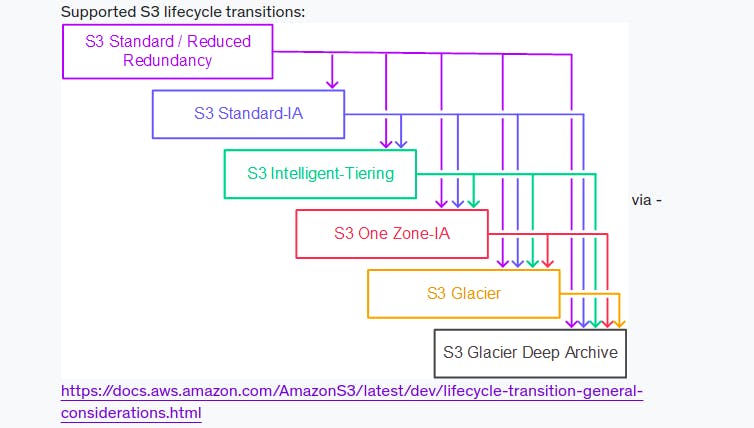
- Objects must be stored at least 30 days in the current storage class before you can transition them to STANDARD_IA or ONEZONE_IA.
- S3 Encryption for Objects: There are 4 methods of encrypting objects in S3
- SSE-S3: encrypts S3 objects using keys handled & managed by AWS
- SSE-KMS: leverage AWS Key Management Service to manage encryption keys, it also provides you with an audit trail
- SSE-C: when you want to manage your own encryption keys
- Client Side Encryption
AWS S3 type
level 1: S3 Standard (durable, immediately available, frequently accessed). level 2: S3 Standard-IA (durable, immediately available, infrequently accessed). level 3: S3 Intelligent Tiering (automatically moves data to the most cost-effective tier). level 4: S3 One Zone-IA: store data in 1 AZ => less resilience but has a lower cost for infrequently access. Can be immediately accessible level 5: S3 Glacier (archived data, retrieval times in minutes or hours). level 6: S3 Glacier Deep Archive (lowest cost storage class for long term retention).
- Amazon S3 Transfer Acceleration enables fast, easy, and secure transfers of files over long distances between your client and an S3 bucket.
- Route 53
- active/passive configuration: => use failover routing policy
- Active-Active Failover
Use this failover configuration when you want all of your resources to be available the majority of the time. When a resource becomes unavailable, Route 53 can detect that it's unhealthy and stop including it when responding to queries.
In active-active failover, all the records that have the same name, the same type (such as A or AAAA), and the same routing policy (such as weighted or latency) are active unless Route 53 considers them unhealthy. Route 53 can respond to a DNS query using any healthy record.
Active-Passive Failover
Use an active-passive failover configuration when you want a primary resource or group of resources to be available the majority of the time and you want a secondary resource or group of resources to be on standby in case all the primary resources become unavailable. When responding to queries, Route 53 includes only the healthy primary resources. If all the primary resources are unhealthy, Route 53 begins to include only the healthy secondary resources in response to DNS queries.
- CNAME: can not create the top node of DNS, only exmple.com. Points a hostname to any other hostname
- ALIAS: can work with ROOT domain, e.g example.com. Points a hostname to an AWS Resource
- geolocation routing policy: sử dụng policy này khi mà muốn serve resource dựa trên location của user
- geoproximity routing policy: sử dụng policy này khi mà muốn oute traffic dựa trên location của resource
- More about Routing Policies
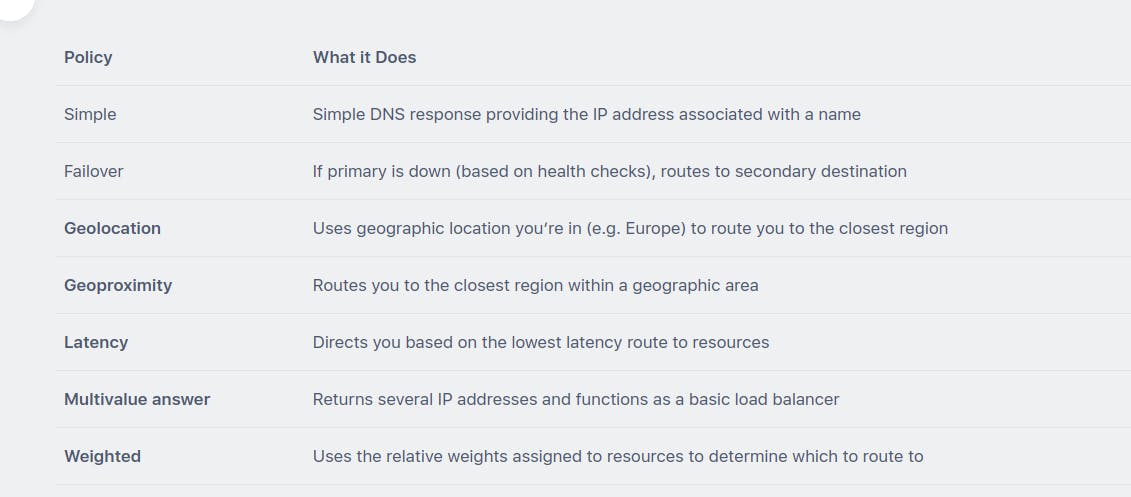
refer: digitalcloud.training/amazon-route-53/#rout..
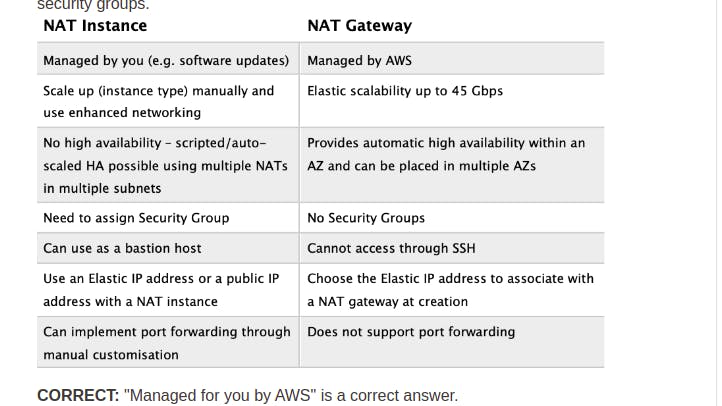
- NAT Gateway, NAT instance
- NAT instance và NAT gateway sinh ra với mục đích các service ben trong private subnet có thể gọi ra bên ngoài internet. Ví dụ DB có thể gọi ra bên ngoài internet để download install package
- VÌ nat gateway đc manage bởi AWS nên khi tạo at gateway chúng ta phải allocate cho nó 1 Elastic IP address, ko giống như NAT instance (chính là 1 EC2 instance nên nó đã có sẵn public IP address)
- Security Groups can be associated with a NAT instance, Nat gateway is NOT
- NAT instance supports port forwarding
- Egress-only internet gateway: only support IPv6
- EC2
- EC2 instance meta data - EC2 instance metadata is data about your instance that you can use to configure or manage the running instance. You cannot use EC2 instance metadata to download log files whenever an instance terminates because of a scale-in event from an auto-scaling policy.
- EC2 instance user data - EC2 instance user data is the data that you specified in the form of a configuration script while launching your instance.
SSD-backed volumes optimized for transactional workloads involving frequent read/write operations with small I/O size, where the dominant performance attribute is IOPS
HDD-backed volumes optimized for large streaming workloads where throughput (measured in MiB/s) is a better performance measure than IOPS
Provision IOPS type supports critical business applications that require sustained IOPS performance, or more than 16,000 IOPS or 250 MiB/s of throughput per volume. Examples are large database workloads, such as: MongoDB Cassandra Microsoft SQL Server MySQL PostgreSQL Oracle
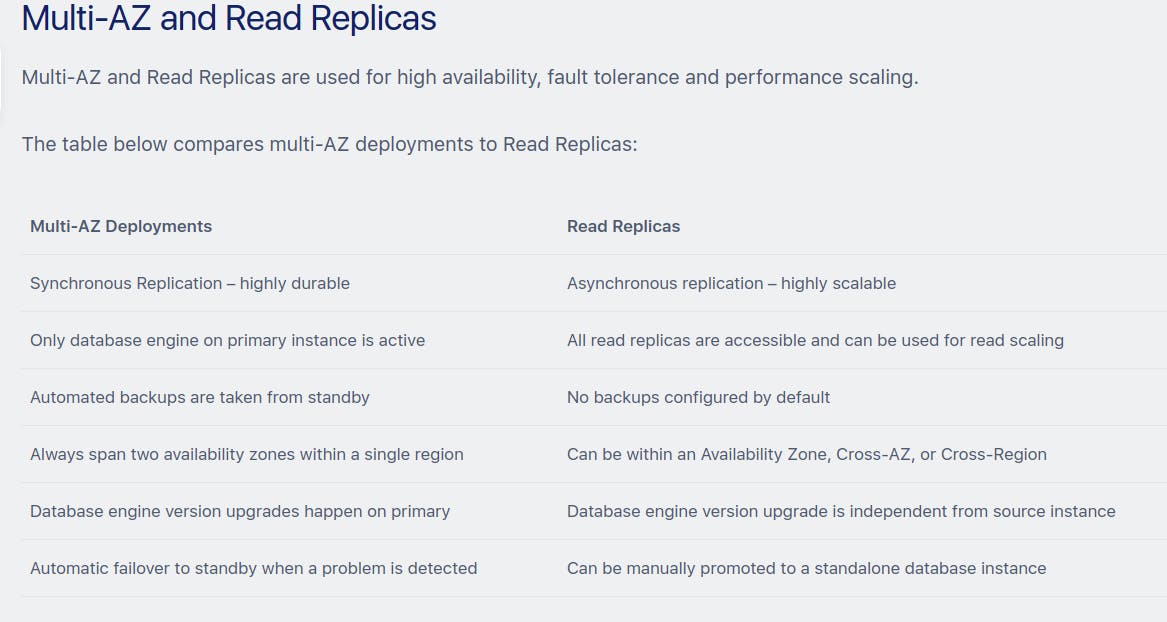
RDS
- Amazon Relational Database Service (Amazon RDS) makes it easy to set up, operate, and scale a relational database in the cloud. It provides cost-efficient and resizable capacity while automating time-consuming administration tasks such as hardware provisioning, database setup, patching, and backups.
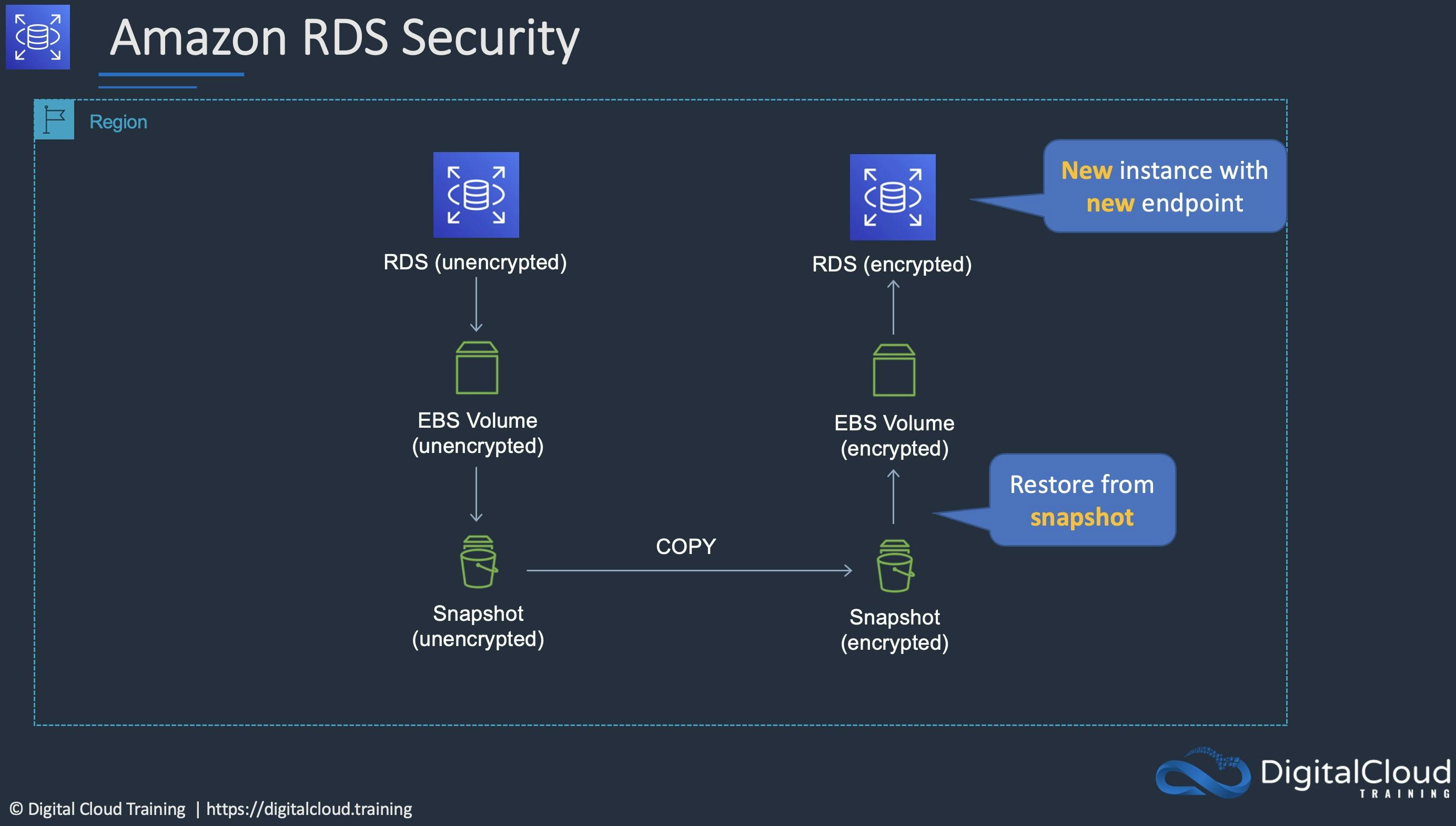
If the master database is encrypted, the read replicas are encrypted
- How to encrypt an existing database: Step 1. Create a snapshot from existing DB instance Step 2: Create an encrypted copy of this snapshot Step 3: Create new DB instance from encrypted snapshot
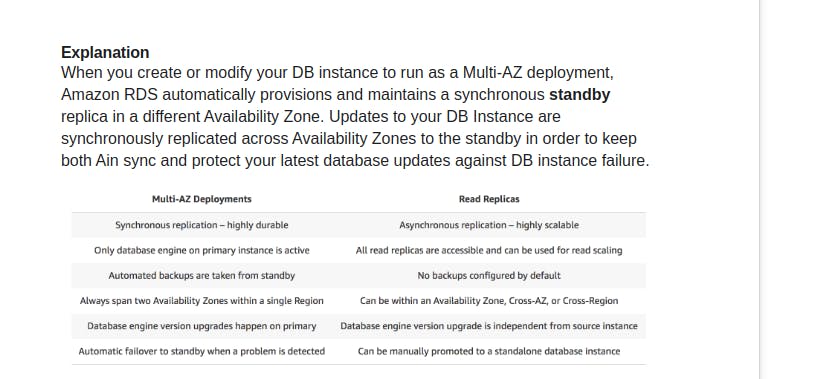
- Run an Amazon RDS DB instance in several AZs with Multi-AZ deployment. Amazon automatically provisions and maintains a secondary standby DB instance in a different AZ.
- Amazon RDS automatically performs a failover in the event of any of the following:
- Loss of availability in primary Availability Zone.
- Loss of network connectivity to primary.
- Compute unit failure on primary
- Storage failure on primary.
Other services:
- Amazon Cognito:
- Identity pools provide AWS credentials to grant your users access to other AWS services.
- User pools: A user pool is a user directory in Amazon Cognito. You can leverage Amazon Cognito User Pools to either provide built-in user management or integrate with external identity providers, such as Facebook, Twitter, Google+, and Amazon.
AWS OpsWorks is a configuration management service that provides managed instances of Chef and Puppet.
AWS Secrets Manager: the service enables you to easily ROTATE, m anage, and retrieve database credentials, API keys, and other secrets throughout their lifecycle.
AWS Step Functions provides serverless orchestration for modern applications. Orchestration centrally manages a workflow by breaking it into multiple steps, adding flow logic, and tracking the inputs and outputs between the steps
- ElastiCache for Redis it's a HIPAA Eligible Service and geopartial support
Amazon ElastiCache for Memcached: Multi-thread ** support
Amazon ElastiCache in-transit encryption is an optional feature that allows you to increase the security of your data at its most vulnerable points
15: Others:
AWS DataSync can be used to MOVE large am ounts of data online between on-premises storage and Amazon S3 or Amazon EFS
Storage Gateway is mainly used in providing low-latency ACCESS to data by caching frequently accessed data on-premises while storing archive data securely and durably in Amazon cloud storage services.
=> Use AWS DataSync to migrate existing data to Amazon S3, and then use the File Gateway to retain access to the migrated data and for ongoing updates from your on-premises file-based applications.
AWS Config is a service that enables you to assess, audit, and evaluate the configurations of your AWS resources.
Amazon GuardDuty is a threat detection service that continuously monitors for malicious activity and unauthorized behavior to protect your AWS accounts, workloads, and data stored in Amazon S3.
- Amazon Macie: uses machine learning and pattern matching to discover and protect your sensitive data on Amazon S3
16: Aurora: An Aurora global database consists of one primary AWS Region where your data is mastered, and up to five read-only, secondary AWS Regions. Aurora replicates data to the secondary AWS Regions with typical latency of under a second.
17: Amazon Redshift Spectrum: query data from S3, it is a data warehouse
Using for query massive datasets and very fast.
18: Direct connect: di kem voi Virtual Private Gateway hoac - A transit gateway when you have multiple VPCs in the same Region. Use Cases: • Increase bandwidth throughput - working with large data sets – lower cost • More consistent network experience - applications using real-time data feeds • Hybrid Environments (on prem + cloud)
- 19: CloudTrail: data events and management event
- CloudTrail provides event history of your AWS account activity, including actions taken through the AWS Management Console, AWS SDKs, command line tools, API calls, and other AWS services. This event history simplifies security analysis, resource change tracking, and troubleshooting.
20: Amazon SNS supports notifications over multiple transport protocols:
HTTP/HTTPS – subscribers specify a URL as part of the subscription registration.
Email/Email-JSON – messages are sent to registered addresses as email (text-based or JSON-object).
SQS – users can specify an SQS standard queue as the endpoint.
SMS – messages are sent to registered phone numbers as SMS text messages.
-21 NACL: A VPC automatically comes with a default network ACL which allows all inbound/outbound traffic. A custom NACL denies all traffic both inbound and outbound by default.
22: Amazon QuickSight is a data visualization tool which will show any IAM permissions-related Access Denied errors and Unauthorized errors.
23: AWS Resource Access Manager (RAM): is a service that enables you to easily and securely share AWS resources with any AWS account or within your AWS Organization. Example: allow EC2 instances in all AWS accounts can communicate to each other via VPC
24: SQS:
- FIFO queues support up to 3,000 messages per second with batching, or up to 300 messages per second
- The name of the FIFO queue ends with the .fifo suffix
- FIFO queues support up to 3,000 messages per second with batching, or up to 300 messages per second
CloudWatch vs CloudTrail vs Config - CloudWatch
+ Available: CPU Utilization, Disk Reads/Writes
+ Custom metrics: memory utilization, Disk space utilization, Disk swap utilization
+ Performance monitoring (metrics, CPU, network, etc…) & dashboards
+ Events & Alerting
+Log Aggregation & Analysis
CloudTrail
- Record API calls made within your Account by everyone
- Can define trails for specific resources
- Global Service
- Risk auditing of your AWS account.
Config
- Record configuration changes
- Evaluate resources against compliance rules
- Get timeline of changes and compliance
AWS STS – Security Token Service: Allows to grant limited and temporary access to AWS resources.
Identity Federation in AWS: Federation lets users outside of AWS to assume temporary role for accessing AWS resources
Disaster recovery strategy:
- Backup and Restore: traditional environments, data is backed up to tape and sent off-site regularly, take longer to restore
- Pilot Light: minimal version of an environment is always running in the cloud
- Warm Standby: Scaled-down version of a fully functional environment is always running in the cloud.
- Hot Site / Multi Site Approach: clone running application
SECURITY:
- Use Web Application Firewall (WAF) with CloudFront distribution
- Protecting against DDOS with Web ACL.
AWS WAF is a web application firewall that helps protect your web applications or APIs against common web exploits that may affect availability, compromise security, or consume excessive resources. AWS WAF gives you control over how traffic reaches your applications by enabling you to create security rules that block common attack patterns, such as SQL injection or cross-site scripting, and rules that filter out specific traffic patterns you define. You can deploy AWS WAF on Amazon CloudFront as part of your CDN solution, the Application Load Balancer that fronts your web servers or origin servers running on EC2, or Amazon API Gateway for your APIs.
To detect and mitigate DDoS attacks, you can use AWS WAF in addition to AWS Shield
Every AWS resource is owned by an AWS account, and permissions to create or access a resource are governed by permissions policies. An account administrator can attach permissions policies to IAM identities (that is, users, groups, and roles), and some services (such as AWS Lambda) also support attaching permissions policies to resources.
Policy: You manage access in AWS by creating policies and attaching them to IAM identities (users, groups of users, or roles) or AWS resources. A policy is an object in AWS that, when associated with an identity or resource, defines their permissions
The following facts apply to IAM Groups:
Groups are collections of users and have policies attached to them.
A group is not an identity and cannot be identified as a principal in an IAM policy.
Use groups to assign permissions to users.
IAM groups cannot be used to group EC2 instances.
Only users and services can assume a role to take on permissions (not groups).
IAM Roles for granting Instance access.
Increasing availability through multi-AZ deployments.
VPC peering
SQS. Having separate queues to provide prioritzation of work.
Kinesis
• Kinesis Data Streams: massively scalable and durable real-time data streaming service
• Kinesis Data Firehose: is the easiest way to reliably load streaming data into data lakes, data stores, and analytics tools.
• Kinesis Data Analytics: analyze data streams with SQL or Apache Flink
• Kinesis Video Streams: capture, process, and store video streams
- Kinesis Data Streams and Firehose.=> outputs will be saved to DynamoDB for near realtime, and miliseconds responsive
- RDS: multi-AZ and Read Replicas are used for high availability, fault tolerance and performance scaling.
RDS Proxy: is a fully managed, highly available database proxy for Amazon Relational Database Service (RDS) => improving database efficiency and application scalability.
